(Updated With New Details) TouchWiz Exploit Can Reset A Device Just By Visiting A Website
Samsung Galaxy S II and S III owners beware as an exploit caused by a single line of code can cause an unstoppable factory reset of your Samsung device. Posted by Pau Oliva earlier in the day, the code was at first only thought to affect the Galaxy S II however, new reports since this morning have indicated that a number of other Samsung devices, including the Galaxy S III suffer from the same exploit.
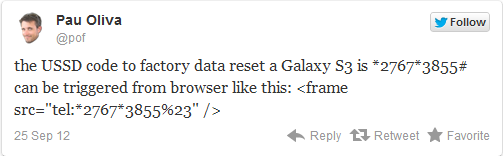
The hack itself is a simple USSD code, that can be sent from a website and triggered by NFC, or a QR code that can cause the device to reset. For now, only Samsung devices running TouchWiz seem to be affected. The danger can run a little deeper if someone were to introduce a USSD code to your device that can both wipe the phone and leave the user with a broken SIM as well.
For now, the advice is to deactivate any automatic site-loading in any QR and/or NFC reader software you have installed on your device. Of course, the safest way to prevent any harm is your own awareness and not clicking on any links you don’t trust. We’d also urge you to use a browser other than the default browser on your Samsung device until a patch is implemented to prevent any harm.
For Galaxy Nexus owners, thanks to your stock Android platform, there is no danger. Also, thanks to TmoNews reader @Jaxidian, who determined that no AOSP based ROM (CM10, AOKP, etc) are vulnerable, nor the leaked TouchWiz Jelly Bean updates for the Galaxy S III.
We’ll keep and eye on this and post any updates as they become available.
More info below:
DroidDog, Pau Oliva, Steve Troughton-Smith, The Verge
Update: As you can see in this video, the Galaxy S III, with the most recent maintenance update is no longer subject to this exploit as a patch has been applied. Furthermore, the exploit is not found in the Galaxy S III Jelly Bean update. Check the video for details: